
Genomes IO
Genomes.io harnesses whole genome sequencing, secure encrypted genomic data storage and blockchain technologies to give users true ownership, security and control over the most valuable and powerful personal dataset they will ever have — their DNA.
The story
As soon as an individual has their genome sequenced they lose control over what happens to the data. It is owned and controlled by third-parties (such as DNA testing companies, national sequencing initiatives, etc) and stored and shared in models that do not ensure security, privacy or equitable compensation for the individual.
The challenge
Putting the power back into the users hands. This means individuals can have their genome sequenced without ever compromising security, privacy or ownership of their data. They are able to privately learn about their own genome, but most importantly contribute anonymised ‘snippets’ of their data to scientific and medical research, and can earn from doing so.
The solution
In our technological solution there are 3 key entities all which communicate with each other to provide fully user-controlled genomic data security to Genomes.io users.
● DNA Vault (container)
● Mobile Application (mobile authenticator)
● Website
DNA Vault
This is where user genomic data is stored. These ‘DNA Vaults’ are fully virtualised containers that run all processes in encrypted memory, encrypting user provided genomic data in storage with private keys provided by their mobile device. These user keys are never stored outside encrypted memory and are only available to the user. The tech stack is built in such a way that means no one, not even Genomes.io as a technology provider, is able to access user ‘DNA Vaults’ and the user always retains full control over their genomic data stored within.
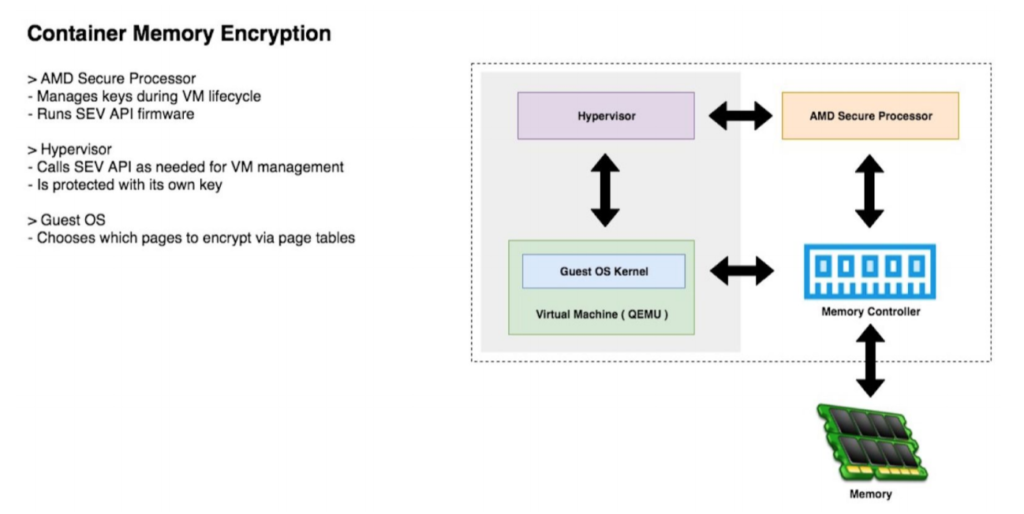
Currently data that is stored in the cloud, especially sensitive personal data (e.g. genomic data), is insecure and liable to data breach/hacks. The data is stored inside virtual machines at data centres hosted by cloud data storage providers (e.g. AWS, Google Cloud, Microsoft Azure). As neither the memory nor hard drive are encrypted, this means these providers have access to the data and can view anything and everything stored within. Secure encryption virtualisation (SEV) technology solves this issue by increasing the level of security in the cloud by providing better security isolation, rooted in the hardware itself. SEV protects data-in-use enabling customer workloads to be protected cryptographically from each other as well as protected from the hosting software. SEV technology is built around a threat model where an attacker is assumed to have access to not only execute user level privileged code on the target machine, but can potentially execute malware at the higher privileged hypervisor level as well. Hackers or even an administrator with malicious intentions at a cloud data center or anyone at Genomes.io are not be able to access the data in a hosted virtual machine.
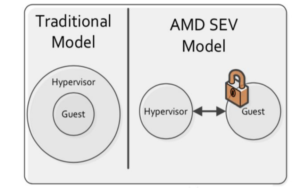
While no security system is 100% secure, SEV significantly reduces the attack surface of VMs in the cloud by encrypting a VM’s memory with a key unique to that VM and unknown to the hypervisor. Many secrets and important information are typically stored in a VM’s memory space and encrypting this content helps prevent attacks and leakage of sensitive data. SEV with Encrypted State (SEV-ES) represents an additional security feature by encrypting and protecting all CPU register contents when a VM stops running. This prevents the leakage of information in CPU registers to components like the hypervisor, and can even detect and prevent malicious modifications to CPU register state. SEV-ES builds upon SEV to provide an even smaller attack surface and additional protection for a guest VM from the hypervisor. Our ‘DNA Vaults’ harness SEV technology, which represents the current gold-standard of cloud-based genomic data storage security. This gives users the ability to securely store their genomic data in the cloud, with confidence that it is never exposed to cloud-computing attacks or administrators with malicious intentions at cloud data centres or even Genomes.io. Our collaboration with Advanced Micro Devices (AMD) will allow us to take advantage of the latest security components available in AMD EPYC processors, such as SEV-ES (when released) to enable full user controlled security of their DNA data. Although there are other solutions (e.g. Intel SGX) that have been developed, harnessing SEV technology permits no application software changes to be required, and with the appropriate operating system or hypervisor modifications, all applications in a system can be protected. Through the use of the hardware VM constructs, SEV is built around the idea of secure sandbox environments where software can execute and is protected from all other software on the system. These sandboxes can be as big as a full VM with its own disk and OS, but they can also be small and used for more fine- grained isolation.
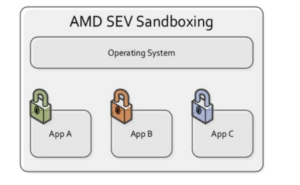
This means genomic analysis software can run inside our ‘DNA Vaults’ without needing to recreate all software into one unified package.
Mobile Application
Our mobile application enables users to communicate with their ‘DNA Vault’ and control all processes on genomic data stored within. Booting a container, running genomic queries and updating the code inside a container all request user permission on their mobile device, and only when permission is provided from the user do they get executed.
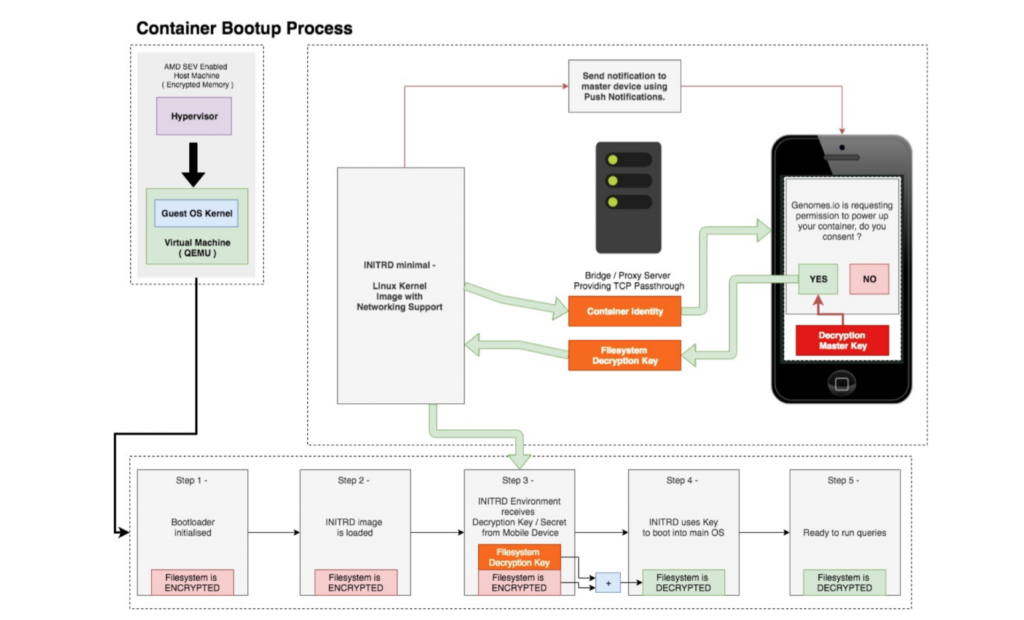
The mobile application acts as an user-controlled authenticator for these processes by containing various private keys including Ethereum, PGP and SSL Certificates. All of which are based on a master seed key generated from 12 keys words, which are given to the user for backup on traditional media during mobile application set up. The mobile application uses these keys for identification, message signing, as well as encryption/decryption of messages and genomic data.
This represents a decentralised solution to user key management with each user actually owning their own private keys, rather than user keys being stored in a centralised system (e.g. Amazon key store, or hardware-based key store), in which anyone in the network can request keys from the store without much effort, and no way for a customer to know this has happened. Our solution relies on the user allowing the system to use those keys should they want to.
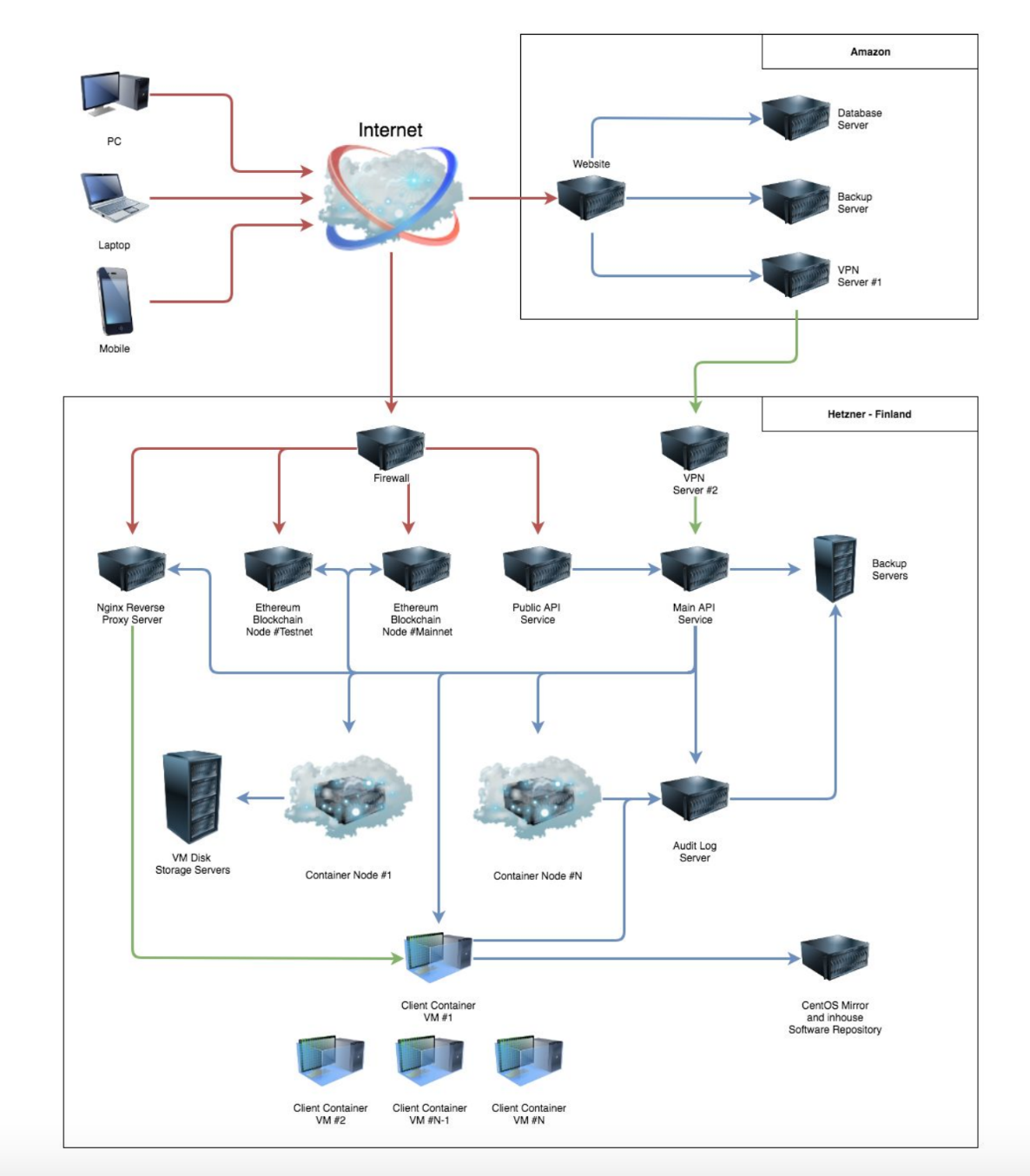
Network Topology
Mark Hahnel
Chief Scientist
BinarZone did an amazing job and we wholeheartedly recommend them as a full-package deal - a team of cutting-edge talent, dedication and passion for development using the latest technologies.